Documentation
¶
Documentation
¶
Overview ¶
Package main is an application package for Findy Agency Service. Please be noted that the whole Findy Agency is still under construction, and there are many missing features for full production use. Also there are some refactoring candidates for restructuring the internal package layout. However, the findy-agent is currently tested for an extended period of pilot and development use, where it's proven to be stable. The current focus of the project is to offer efficient and straightforward multi-tenant agency with Aries compatible agent protocols.
You can use the agency and related Go packages roughly for four purposes:
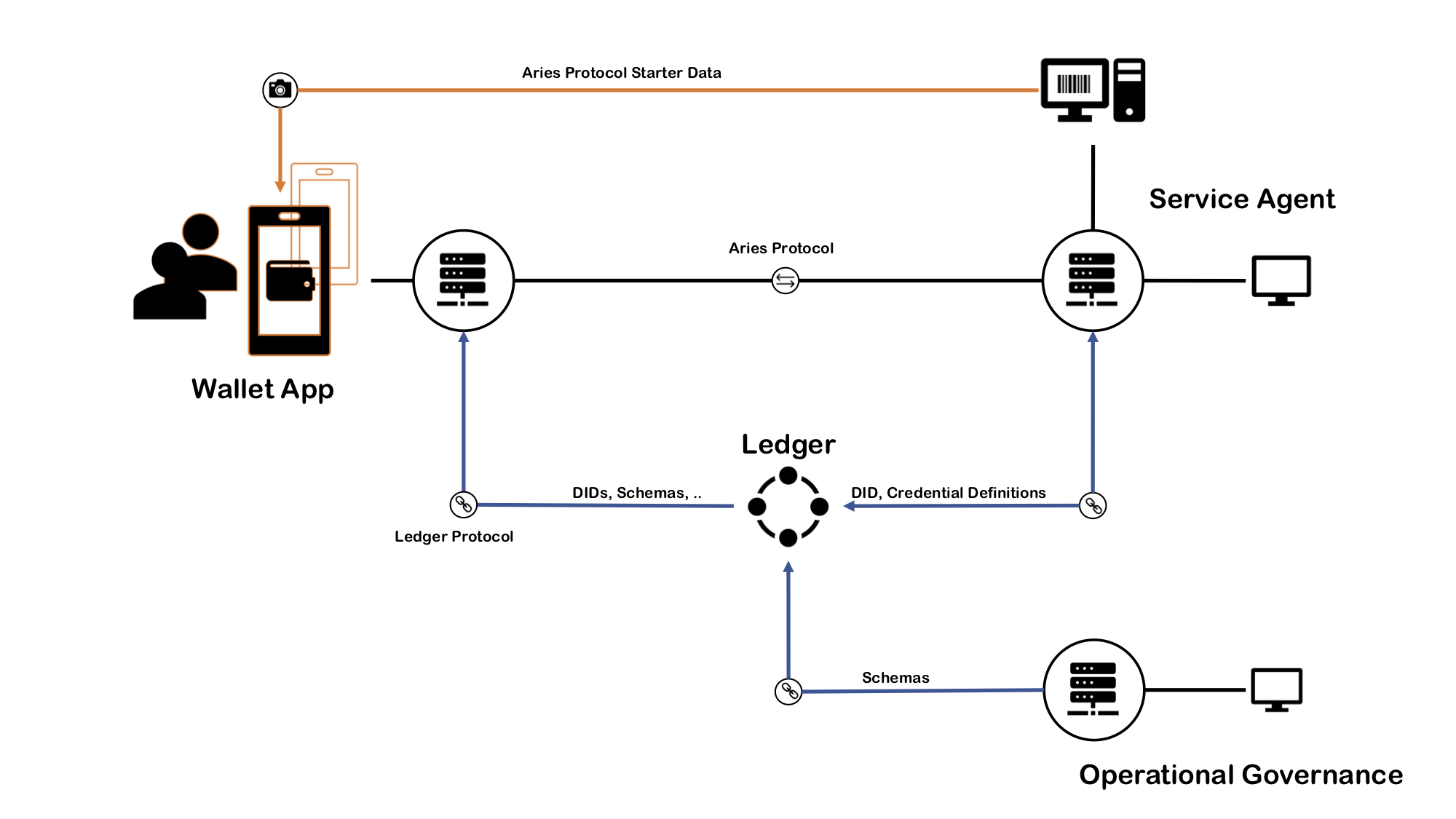
1. As a service agency for multiple Edge Agents at the same time by implementing them corresponding Cloud Agents. Allocated CAs implement Aries agent to agent protocols and interoperability.
2. As a CLI tool for setting up Edge Agent wallets, creating schemas and credential definitions into the wallet and writing them to the ledger. You can use findy-agent's own CLI for most of the needed tasks but for be usability we recommend to use findy CLI.
3. As an admin tool to monitor and maintain agency.
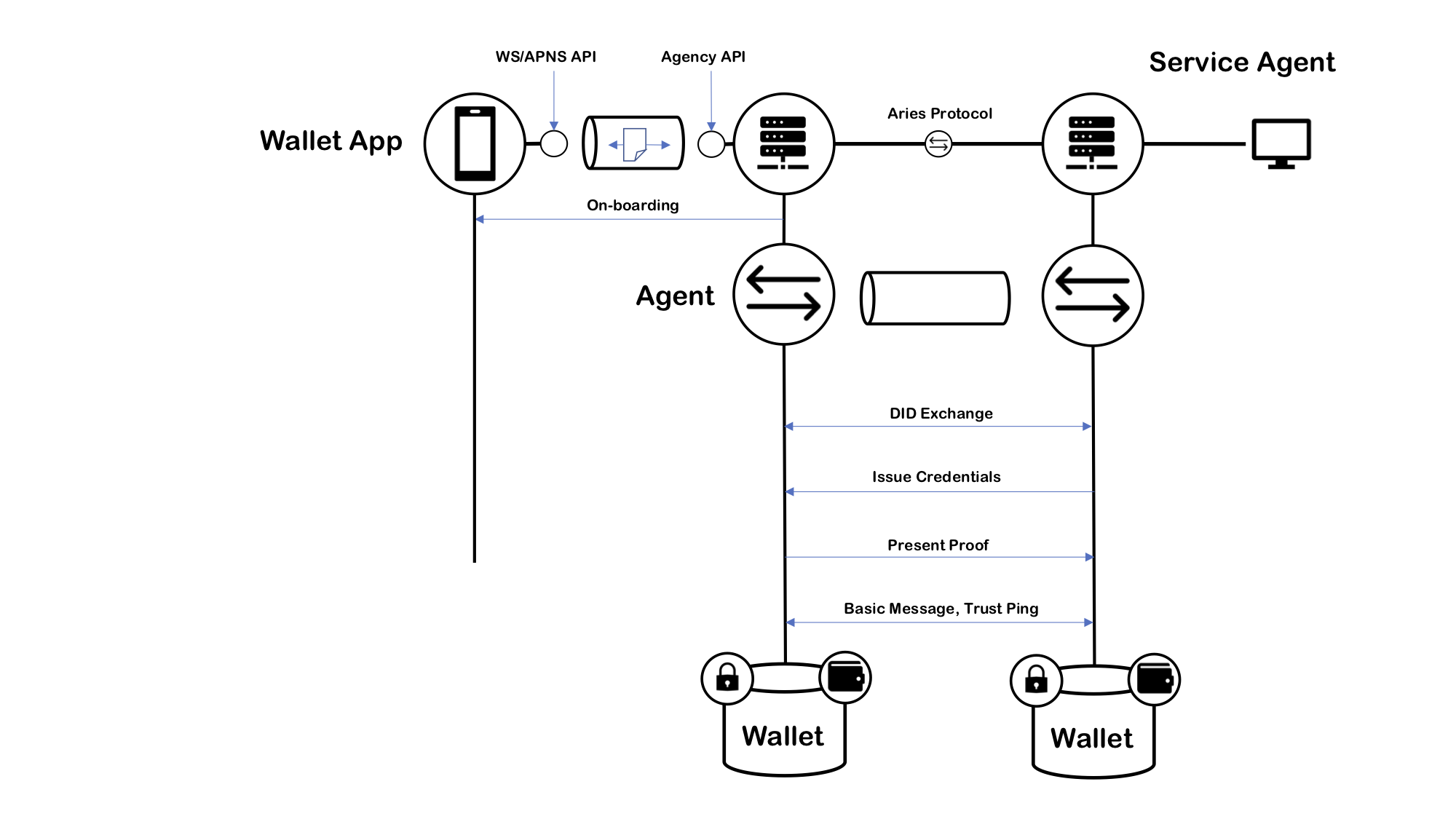
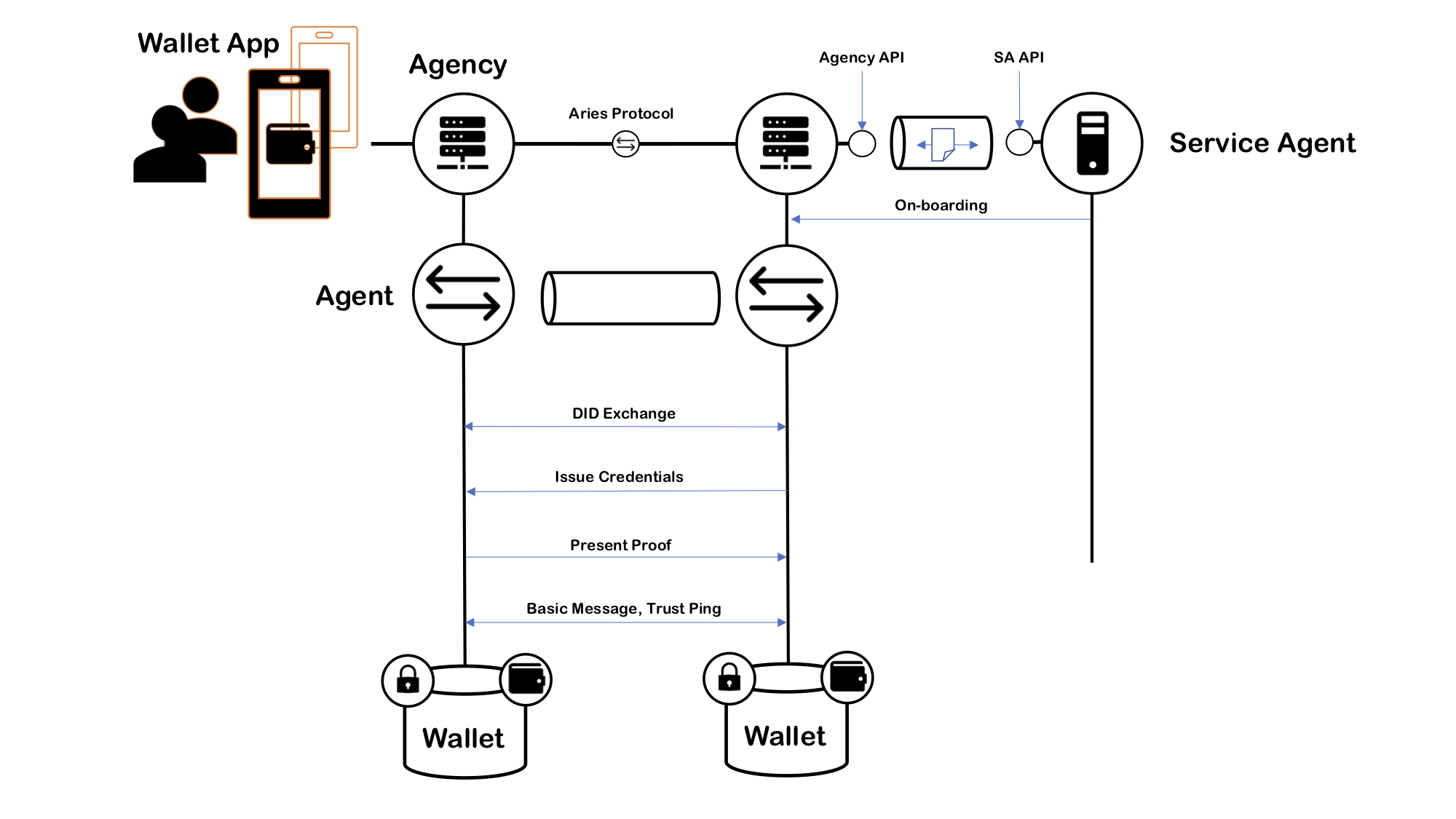
4. As a framework to implement Service Agents like issuers and verifiers. There are Go helpers to onboard EAs to agency and the Client, which hides the connections to the agency.
About the build-in CLI ¶
The agency's compilation includes command and flag sets to operate it with minimal dependencies to other repos or utilities. The offered command set is minimal, but it offers everything to set up and maintain an agency. There is a separate CLI UI in other repo, which includes an extended command set with auto-completion scripts.
Documentation ¶
The whole codebase is still heavily under construction, but the main principles are ready and ok. Documentation is very minimal and partially missing.
Sub-packages ¶
findy-agent can be used as a service, as a framework and a CLI tool. It's structured to the following sub-packages:
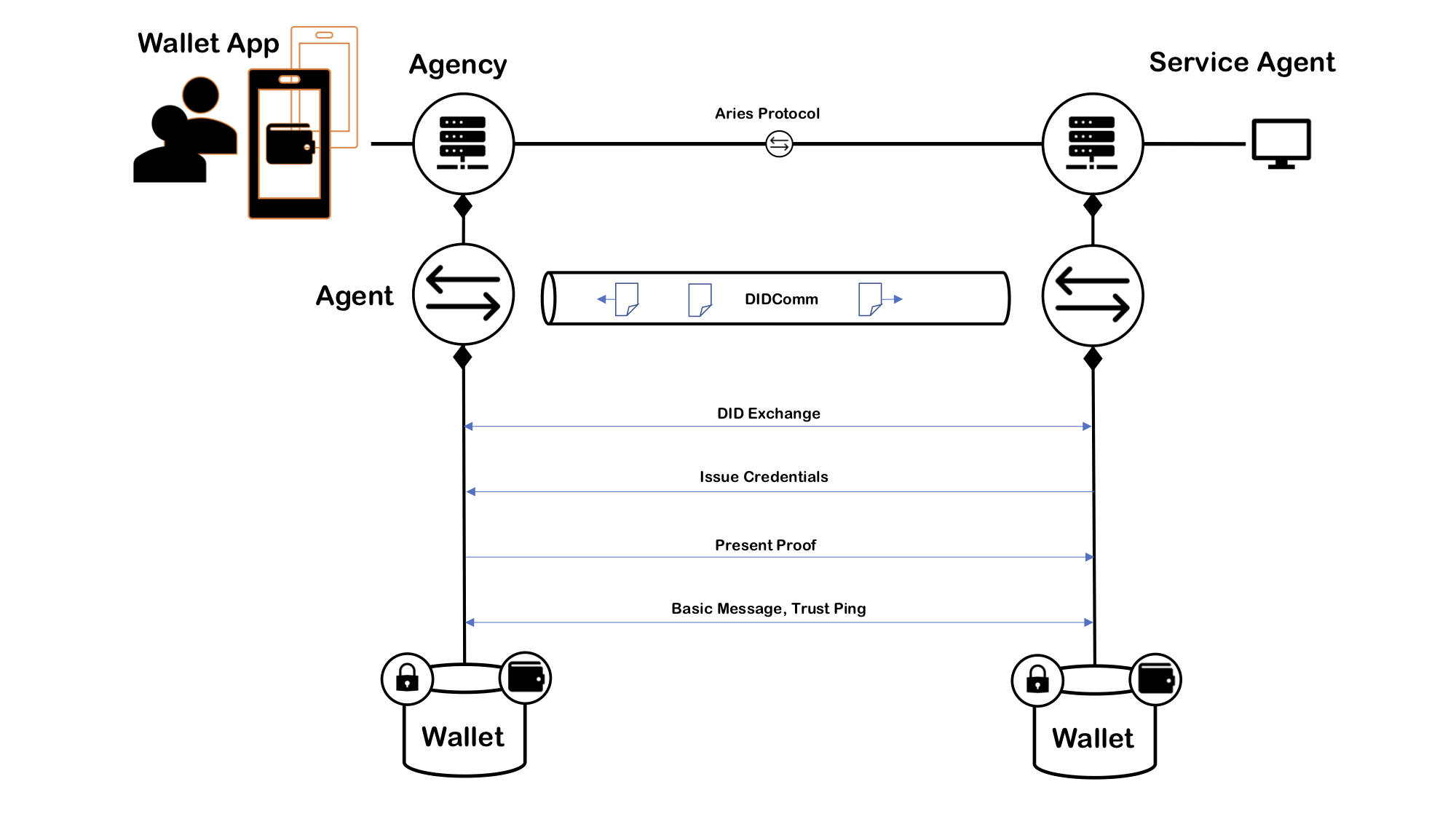
agent includes framework packages like agency, agents, didcomm, endp, .. client is a package to connect the agency from remote enclave implements a secure enclave (interfaces) for the server protocol includes processors for Aries agent-to-agent protocols server implements the http server for APIs, endpoints, etc. std a root package for Aries protocol messages
 Directories
¶
Directories
¶
| Path | Synopsis |
|---|---|
|
Package agent is a package for the cloud agent and its services.
|
Package agent is a package for the cloud agent and its services. |
|
agency
Package agency offers mainly internal services for Agency framework to help implement multi tenant agent service.
|
Package agency offers mainly internal services for Agency framework to help implement multi tenant agent service. |
|
aries
Package aries is implementation package for didcomm messages.
|
Package aries is implementation package for didcomm messages. |
|
didcomm
Package didcomm is package to offer interfaces for all types of the didcomm messages.
|
Package didcomm is package to offer interfaces for all types of the didcomm messages. |
|
handshake
Package handshake is abstraction for agency level handshake protocol which on-boards new clients to the agency.
|
Package handshake is abstraction for agency level handshake protocol which on-boards new clients to the agency. |
|
mesg
Package mesg is implementation package for didcomm messages.
|
Package mesg is implementation package for didcomm messages. |
|
Package enclave is a server-side Secure Enclave.
|
Package enclave is a server-side Secure Enclave. |
|
server
Package server is a playground where we have tried gRPC interface for CA API.
|
Package server is a playground where we have tried gRPC interface for CA API. |
|
Package plugins is general purpose package for findy-agent to register addons for agency as a Go code without direct dependency to the implementation and to the repo.
|
Package plugins is general purpose package for findy-agent to register addons for agency as a Go code without direct dependency to the implementation and to the repo. |
|
Package protocol is package for Aries protocol processors.
|
Package protocol is package for Aries protocol processors. |
|
issuecredential/preview
Package preview implements helpers for Aries issuing protocol.
|
Package preview implements helpers for Aries issuing protocol. |
|
presentproof
Package presentproof is Aries protocol processor for present proof protocol.
|
Package presentproof is Aries protocol processor for present proof protocol. |
|
presentproof/preview
Package preview includes helpers for Aries present proof protocol processor.
|
Package preview includes helpers for Aries present proof protocol processor. |
|
presentproof/prover
Package prover includes Aries protocol handlers for a prover.
|
Package prover includes Aries protocol handlers for a prover. |
|
presentproof/verifier
Package verifier includes Aries protocol handlers for a verifier.
|
Package verifier includes Aries protocol handlers for a verifier. |
|
Package server encapsulates http server entry points.
|
Package server encapsulates http server entry points. |
|
Package std is package for standard files.
|
Package std is package for standard files. |
|
didexchange
Package didexchange is currently used for connection protocol implementation
|
Package didexchange is currently used for connection protocol implementation |
|
didexchange/invitation
Package invitation is for invitation data model.
|
Package invitation is for invitation data model. |
|
issuecredential
Package issuecredential is package for Aries protocol messages for same name.
|
Package issuecredential is package for Aries protocol messages for same name. |