Alaz - Ddosify eBPF Agent
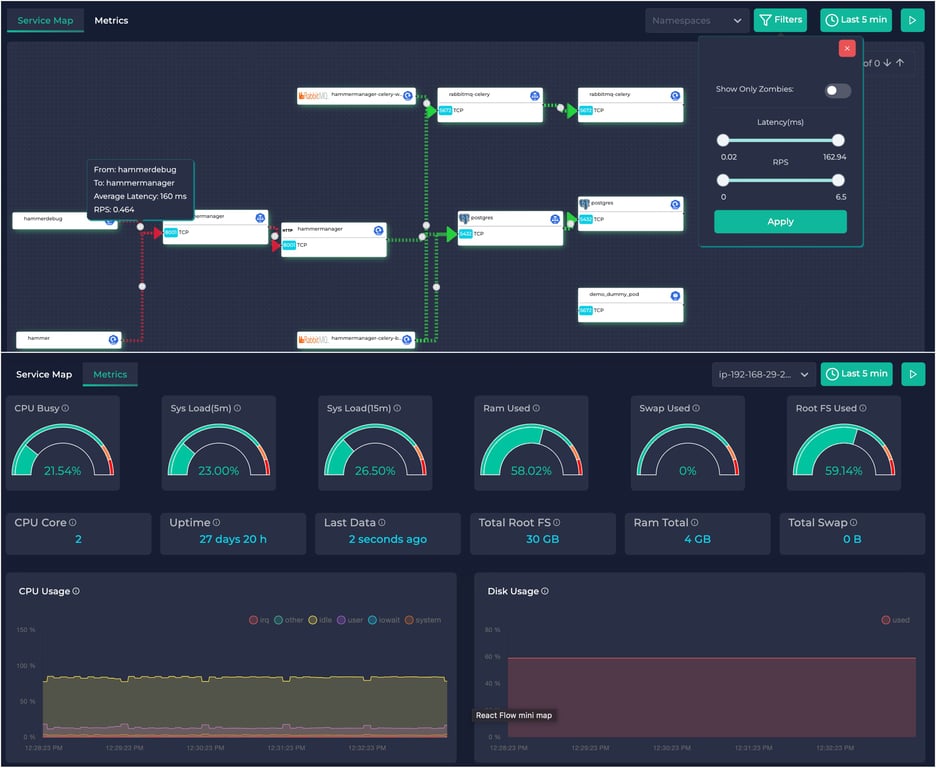



Alaz is an open-source Ddosify eBPF agent that can inspect and collect Kubernetes (K8s) service traffic without the need for code instrumentation, sidecars, or service restarts. This is possible due to its use of eBPF technology. Alaz can create a Service Map that helps identify golden signals and problems like high latencies, 5xx errors, zombie services, SQL queries. Additionally, it can gather system information and resources via the Prometheus Node Exporter, which is readily available on the agent. Alaz Docker image is available on Docker Hub.
➡️ For more information about Ddosify, see Ddosify.
Features
✅ Low-Overhead:
Inspect and collect K8s service traffic without the need for code instrumentation, sidecars, or service restarts.
✅ Effortless:
Ddosify will create the Service Map & Metrics Dashboard that helps identify golden signals and issues such as high latencies, 5xx errors, zombie services.
✅ Prometheus Compatible:
Gather system information and resources via the Prometheus Node Exporter, which is readily available on the agent.
✅ Cloud or On-premise:
Export metrics to Ddosify Cloud, or install the Ddosify Self-Hosted in your infrastructure and manage everything according to your needs.
✅ Test & Observe:
Ddosify Performance Testing and Alaz can work collaboratively. You can start a load test and monitor your system simultaneously. This will help you spot performance issues instantly. Check out the Ddosify GitHub Repository for more information about Ddosify Stack.
✅ Works on both Arm64 and x86_64 architectures.
Getting Started
To use Alaz, you need to have a Ddosify Cloud account or Ddosify Self-Hosted installed.
☁️ For Ddosify Cloud
- Register for a Ddosify Cloud account.
- Add a cluster on the Observability page. You will receive a Monitoring ID and instructions.
- Run the agent on your Kubernetes cluster using the instructions you received. There are two options for Kubernetes deployment:
Using the kubectl
# Replace <MONITORING_ID> with your monitoring ID from the Ddosify Cloud. Change XXXXX with your monitoring ID.
MONITORING_ID=XXXXX
curl -sSL https://raw.githubusercontent.com/ddosify/alaz/master/resources/alaz.yaml -o alaz.yaml
sed -i"" -e "s/<MONITORING_ID>/$MONITORING_ID/g" alaz.yaml
kubectl create namespace ddosify
kubectl apply -f alaz.yaml
Using the Helm
# Replace <MONITORING_ID> with your monitoring ID from the Ddosify Cloud. Change XXXXX with your monitoring ID.
MONITORING_ID=XXXXX
helm repo add ddosify https://ddosify.github.io/ddosify-helm-charts/
helm repo update
kubectl create namespace ddosify
helm upgrade --install --namespace ddosify alaz ddosify/alaz --set monitoringID=$MONITORING_ID
Then you can view the metrics and Kubernetes Service Map on the Ddosify Observability dashboard. For more information, see Ddosify Observability Docs.
🏠 For Ddosify Self-Hosted
- Install Ddosify Self-Hosted
- Add a cluster on the Observability page of your Self-Hosted frontend. You will receive a Monitoring ID and instructions.
- Run the agent on your Kubernetes cluster using the instructions you received.
Note: After you install Ddosify Self-Hosted, you will have a Ddosify Self-Hosted endpoint of nginx reverse proxy. The base URL of the Ddosify Self-Hosted endpoint forwards traffic to the frontend. The base URL of the Ddosify Self-Hosted endpoint with /api suffix forwards traffic to the backend. So you need to set the backend host variable as http://<your-ddosify-self-hosted-endpoint>/api.
There are two options for Kubernetes deployment:
Using the kubectl
# Replace <MONITORING_ID> with your monitoring ID from the Ddosify Cloud. Change XXXXX with your monitoring ID.
MONITORING_ID=XXXXX
# Set BACKEND_HOST with your Ddosify Self Hosted Endpoint. If your Ddosify Self Hosted endpoint is http://localhost:8014, then BACKEND_HOST=localhost:8014
BACKEND_HOST=XXXXX
curl -sSL https://raw.githubusercontent.com/ddosify/alaz/master/resources/alaz.yaml -o alaz.yaml
sed -i"" -e "s/<MONITORING_ID>/$MONITORING_ID/g" alaz.yaml
sed -i"" -e "s/https:\/\/api.ddosify.com:443/http:\/\/$BACKEND_HOST\/api/g" alaz.yaml
kubectl create namespace ddosify
kubectl apply -f alaz.yaml
Using the Helm
# Replace <MONITORING_ID> with your monitoring ID from the Ddosify Cloud. Change XXXXX with your monitoring ID.
MONITORING_ID=XXXXX
# Set BACKEND_HOST with your Ddosify Self Hosted Endpoint. If your Ddosify Self Hosted endpoint is http://localhost:8014, then BACKEND_HOST=http://localhost:8014/api
BACKEND_HOST=XXXXX
helm repo add ddosify https://ddosify.github.io/ddosify-helm-charts/
helm repo update
kubectl create namespace ddosify
helm upgrade --install --namespace ddosify alaz ddosify/alaz --set monitoringID=$MONITORING_ID --set backendHost=$BACKEND_HOST
Then you can view the metrics and Kubernetes Service Map on the Ddosify Self-Hosted Observability dashboard. For more information, see Ddosify Observability Docs.
Alaz runs as a DaemonSet on your Kubernetes cluster. It collects metrics and sends them to Ddosify Cloud or Ddosify Self-Hosted. You can view the metrics on the Ddosify Observability dashboard. For the detailed Alaz architecture, see Alaz Architecture.
Cleanup
To remove Alaz from your Kubernetes cluster, run the following command:
kubectl delete -f https://raw.githubusercontent.com/ddosify/alaz/master/resources/alaz.yaml
helm delete alaz --namespace ddosify
Supported Protocols
Alaz supports the following protocols:
- HTTP
- HTTPS (OpenSSL and Go TLS)
- Postgres
- RabbitMQ
Other protocols will be supported soon.
Limitations
Alaz runs on Linux Kubernetes clusters. Windows or MacOS are not supported.
In the future, we plan to support Docker containers.
Alaz is an eBPF application that uses CO-RE.
Most of the latest linux distributions support CO-RE. In order to CO-RE to work, the kernel has to built with BTF(bpf type format) information.
You can check your kernel version with uname -r
command and whether btf is enabled by default or not at the btfhub.
For the time being, we expect that btf information is readily available on your system. We'll support all kernels in the upcoming weeks leveraging btfhub.
Encryption Libraries
These are the libraries that alaz hooks into for capturing encrypted traffic.
-
crypto/tls:
In order to Alaz to capture tls requests in your Go applications, your go version must be 1.17+ and your executable must include debug info.
-
OpenSSL:
OpenSSL shared objects that is dynamically linked into your executable is supported.
Supported versions : 1.0.2, 1.1.1 and 3.*
Contributing
Contributions to Alaz are welcome! To contribute, please follow these steps:
- Fork the repository
- Create a new branch:
git checkout -b my-branch
- Make your changes and commit them:
git commit -am 'Add some feature'
- Push to the branch:
git push origin my-branch
- Submit a pull request
Communication
You can join our Discord Server for issues, feature requests, feedbacks or anything else.
License
Alaz is licensed under the AGPLv3: https://www.gnu.org/licenses/agpl-3.0.html