Documentation
¶
Documentation
¶
Overview ¶
Package teler provides implementations of teler IDS middleware.
teler IDS is a web application firewall that protects against a variety of web-based attacks. The middleware implementations in this package can be used to protect Go-based web applications from these attacks.
To use the middleware implementations in this package, simply import the package and then use the appropriate middleware function to create a new middleware instance. The middleware instance can then be used to wrap an existing HTTP handler.
Index ¶
- Constants
- type Condition
- type Options
- type Response
- type Rule
- type Teler
- func (t *Teler) Analyze(w http.ResponseWriter, r *http.Request) error
- func (t *Teler) CaddyHandler(h caddyhttp.Handler) caddyhttp.HandlerFunc
- func (t *Teler) CaddyHandlerFuncWithNext(w http.ResponseWriter, r *http.Request, next caddyhttp.HandlerFunc) error
- func (t *Teler) Handler(h http.Handler) http.Handler
- func (t *Teler) HandlerFuncWithNext(w http.ResponseWriter, r *http.Request, next http.HandlerFunc)
- func (t *Teler) SetHandler(handler http.Handler)
- type Threat
- type UpdateOptions
Examples ¶
Constants ¶
const ( DefaultStatusResponse = 403 DefaultHTMLResponse = `` /* 1198-byte string literal not displayed */ )
Variables ¶
This section is empty.
Functions ¶
This section is empty.
Types ¶
type Condition ¶
type Condition struct {
// Method is the HTTP method to match against.
// It is of type request.Method, which is a type alias for string.
//
// It will be ignored if DSL is not empty.
Method request.Method `json:"method" yaml:"method"`
// Element is the request element to match.
// These element are defined in the request.Element type.
//
// When you specify the definition using JSON or YAML, the value
// is an `int` that corresponds to the following representations:
// - `0` represents [request.URI]
// - `1` represents [request.Headers]
// - `2` represents [request.Body]
// - `3` represents [request.Any]
//
// It will be ignored if DSL is not empty.
Element request.Element `json:"element" yaml:"element"`
// Pattern is the regular expression to match against the element.
//
// It will be ignored if DSL is not empty.
Pattern string `json:"pattern" yaml:"pattern"`
// DSL is the DSL expression to match against the incoming requests.
DSL string `json:"dsl" yaml:"dsl"`
// contains filtered or unexported fields
}
Condition specifies a request element to match and a pattern or DSL expression to match against the element.
type Options ¶
type Options struct {
// Excludes is a list of threat types to exclude from the security checks.
// These threat types are defined in the threat.Threat type.
//
// When you specify the definition using JSON or YAML, the value
// is an `int` that corresponds to the following representations:
// - `0` represents [Threat.Custom]
// - `1` represents [Threat.CommonWebAttack]
// - `2` represents [Threat.CVE]
// - `3` represents [Threat.BadIPAddress]
// - `4` represents [Threat.BadReferrer]
// - `5` represents [Threat.BadCrawler]
// - `6` represents [Threat.DirectoryBruteforce]
Excludes []threat.Threat `json:"excludes" yaml:"excludes"`
// Whitelists is a list of DSL expressions that match request elements
// that should be excluded from the security checks.
Whitelists []string `json:"whitelists" yaml:"whitelists"`
// Customs is a list of custom security rules to apply to incoming requests.
//
// These rules can be used to create custom security checks or to override
// the default security checks provided by teler-waf.
Customs []Rule `json:"customs" yaml:"customs"`
// CustomsFromFile specifies the file path or glob pattern for loading custom
// security rules. These rules can be used to create custom security checks
// or to override the default security checks provided by teler IDS.
//
// The glob pattern supports wildcards, allowing you to specify multiple files
// or a directory with matching files. For example, "/path/to/custom/rules/**/*.yaml"
// will load all YAML files in the "rules" directory and its subdirectories.
CustomsFromFile string `json:"customs_from_file" yaml:"customs_from_file"`
// Response is the configuration for custom error response pages when a request
// is blocked or rejected.
Response Response `json:"response" yaml:"response"`
// LogFile is the file path for the log file to store the security logs.
//
// If LogFile is specified, log messages will be written to the specified
// file in addition to stderr (if NoStderr is false).
LogFile string `json:"log_file" yaml:"log_file"`
// LogWriter is an io.Writer interface used for custom log message output.
//
// By default, log messages are written to the standard error (stderr) if
// NoStderr is set to false. However, you can customize the output destination
// for log messages by providing your own implementation of io.Writer to this
// field. When a custom LogWriter is assigned, log messages will be written to
// it in addition to LogFile and stderr (if NoStderr is false). This allows you
// to capture and handle log messages in a custom way, such as sending them to
// a remote logging service, storing them in a database, or handling them in a
// specialized manner.
LogWriter io.Writer `json:"-" yaml:"-"`
// NoStderr is a boolean flag indicating whether or not to suppress log messages
// from being printed to the standard error (stderr) stream.
//
// When set to true, log messages will not be printed to stderr. If set to false,
// log messages will be printed to stderr. By default, log messages are printed
// to stderr (false).
NoStderr bool `json:"no_stderr" yaml:"no_stderr"`
// NoUpdateCheck is a boolean flag indicating whether or not to disable automatic threat
// dataset updates.
//
// When set to true, automatic updates will be disabled. If set to false, automatic
// updates will be enabled. By default, automatic updates are enabled (false).
//
// If the InMemory is set to true, the NoUpdateCheck value will not have any effect
// or automatic updates will always be enabled.
NoUpdateCheck bool `json:"no_update_check" yaml:"no_update_check"`
// Development is a boolean flag that determines whether the request is cached or not.
//
// By default, development mode is disabled (false) or requests will cached.
Development bool `json:"development" yaml:"development"`
// InMemory is a boolean flag that specifies whether or not to load the threat dataset
// into memory on initialization.
//
// When set to true, the threat dataset will be loaded into memory, which can be useful
// when running your service or application on a distroless or runtime image, where file
// access may be limited or slow. If InMemory is set to false, the threat dataset will
// be downloaded and stored under the user-level cache directory on the first startup.
// Subsequent startups will use the cached dataset.
InMemory bool `json:"in_memory" yaml:"in_memory"`
// FalcoSidekickURL is the URL of the FalcoSidekick endpoint to which teler-waf's events
// will be forwarded.
//
// This field should be set to the URL of your FalcoSidekick instance, including the
// protocol & port (e.g. "http://localhost:2801").
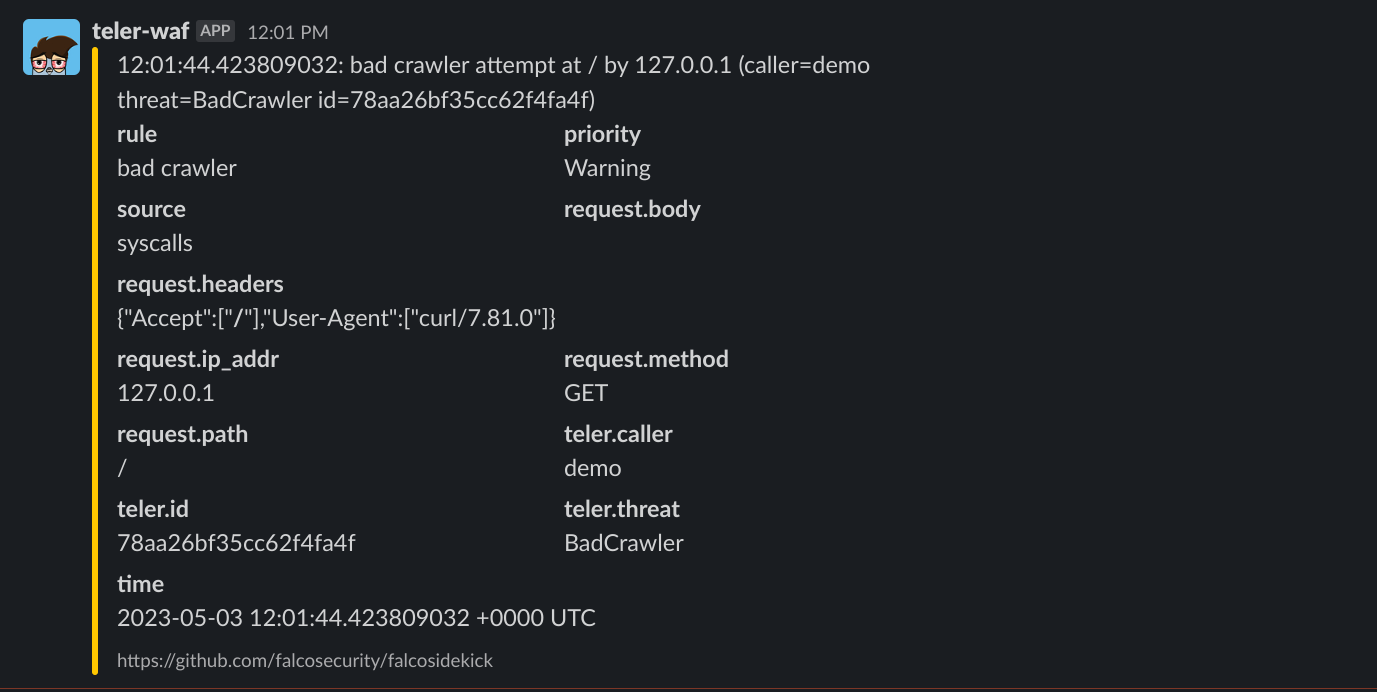
FalcoSidekickURL string `json:"falcosidekick_url" yaml:"falcosidekick_url"`
// Verbose is a boolean flag that controls whether verbose logging is enabled.
// When set to true, it enables detailed and informative logging messages.
Verbose bool `json:"verbose" yaml:"verbose"`
}
Options is a struct for specifying configuration options for the teler.Teler middleware.
type Response ¶
type Response struct {
// Status defines the HTTP status code to be used in the response when a
// request is blocked or rejected. Default is using DefaultStatusResponse.
Status int `json:"status" yaml:"status"`
// HTML defines the custom HTML response page that will be sent when
// a request is blocked or rejected. This field allows you to specify the HTML
// content directly as a string. It will be ignored if HTMLFile is set.
// Beware that we DO NOT escape the HTML content.
// Default is using DefaultHTMLResponse.
HTML string `json:"html" yaml:"html"`
// HTMLFile specifies the path to a file containing the custom HTML
// response page. The contents of this file will be used as the custom response
// page when a request is blocked or rejected. Beware that we DO NOT escape the
// HTML content.
HTMLFile string `json:"html_file" yaml:"html_file"`
}
Response represents the configuration for custom error response pages when a request is blocked or rejected.
type Rule ¶
type Rule struct {
// Name is the name of the rule.
Name string `json:"name" yaml:"name"`
// Condition specifies the logical operator to use when evaluating the
// rule's conditions. Valid values are "and" and "or".
Condition string `json:"condition" yaml:"condition"`
// Rules is a list of conditions that must be satisfied for the rule to
// be triggered. Each condition specifies a request element to match and
// a pattern to match against the element.
Rules []Condition `json:"rules" yaml:"rules"`
}
Rule is custom security rules to apply to incoming requests.
type Teler ¶
type Teler struct {
// contains filtered or unexported fields
}
Teler is a middleware that helps setup a few basic security features
func New ¶
New constructs a new Teler instance with the supplied options.
Example (Custom) ¶
var myHandler = http.HandlerFunc(func(w http.ResponseWriter, r *http.Request) {
_, _ = w.Write([]byte("hello world"))
})
telerMiddleware := New(Options{
Excludes: []threat.Threat{
threat.BadReferrer,
threat.BadCrawler,
},
Whitelists: []string{
`request.Headers matches "(curl|Go-http-client|okhttp)/*" && threat == BadCrawler`,
`request.URI startsWith "/wp-login.php"`,
`request.IP in ["127.0.0.1", "::1", "0.0.0.0"]`,
`request.Headers contains "authorization" && request.Method == "POST"`,
},
Customs: []Rule{
{
Name: "Log4j Attack",
Condition: "or",
Rules: []Condition{
{
Method: request.GET,
// if Method is not set or invalid, defaulting to request.GET.
Element: request.URI,
// you can use request.Any: it useful when you want to
// match against multiple elements of the request at once,
// rather than just a single element.
Pattern: `\$\{.*:\/\/.*\/?\w+?\}`,
},
},
},
},
LogFile: "/tmp/teler.log",
})
app := telerMiddleware.Handler(myHandler)
go func() {
_ = http.ListenAndServe("127.0.0.1:3000", app)
}()
Output:
Example (Default) ¶
var myHandler = http.HandlerFunc(func(w http.ResponseWriter, r *http.Request) {
_, _ = w.Write([]byte("hello world"))
})
telerMiddleware := New()
app := telerMiddleware.Handler(myHandler)
go func() {
_ = http.ListenAndServe("127.0.0.1:3000", app)
}()
Output:
Example (SetHandler) ¶
var forbidden = http.HandlerFunc(func(w http.ResponseWriter, r *http.Request) {
http.Error(w, "We're sorry, but your request has been denied for security reasons.", http.StatusForbidden)
})
var myHandler = http.HandlerFunc(func(w http.ResponseWriter, r *http.Request) {
_, _ = w.Write([]byte("hello world"))
})
telerMiddleware := New()
telerMiddleware.SetHandler(forbidden)
app := telerMiddleware.Handler(myHandler)
go func() {
_ = http.ListenAndServe("127.0.0.1:3000", app)
}()
Output:
func Update ¶
func Update(opts ...UpdateOptions) *Teler
func (*Teler) CaddyHandler ¶
func (t *Teler) CaddyHandler(h caddyhttp.Handler) caddyhttp.HandlerFunc
CaddyHandler is a special HTTP handler implementation for Caddy.
func (*Teler) CaddyHandlerFuncWithNext ¶
func (t *Teler) CaddyHandlerFuncWithNext(w http.ResponseWriter, r *http.Request, next caddyhttp.HandlerFunc) error
CaddyHandlerFuncWithNext is a special implementation for Caddy.
func (*Teler) Handler ¶
Handler implements the http.HandlerFunc for integration with the standard net/http library.
func (*Teler) HandlerFuncWithNext ¶
func (t *Teler) HandlerFuncWithNext(w http.ResponseWriter, r *http.Request, next http.HandlerFunc)
HandlerFuncWithNext is a special implementation for Negroni, but could be used elsewhere.
func (*Teler) SetHandler ¶
SetHandler sets the handler to call when the teler rejects a request.
type Threat ¶
type Threat struct {
// contains filtered or unexported fields
}
Threat defines what threat category should be excluded and what is the corresponding data.
type UpdateOptions ¶
type UpdateOptions struct {
// Excludes is a list of threat types to exclude from the security checks.
// These threat types are defined in the threat.Threat type.
//
// When you specify the definition using JSON or YAML, the value
// is an `int` that corresponds to the following representations:
// - `0` represents [Threat.Custom]
// - `1` represents [Threat.CommonWebAttack]
// - `2` represents [Threat.CVE]
// - `3` represents [Threat.BadIPAddress]
// - `4` represents [Threat.BadReferrer]
// - `5` represents [Threat.BadCrawler]
// - `6` represents [Threat.DirectoryBruteforce]
Excludes []threat.Threat `json:"excludes" yaml:"excludes"`
// Whitelists is a list of DSL expressions that match request elements
// that should be excluded from the security checks.
Whitelists []string `json:"whitelists" yaml:"whitelists"`
// Customs is a list of custom security rules to apply to incoming requests.
//
// These rules can be used to create custom security checks or to override
// the default security checks provided by teler-waf.
Customs []Rule `json:"customs" yaml:"customs"`
// CustomsFromFile specifies the file path or glob pattern for loading custom
// security rules. These rules can be used to create custom security checks
// or to override the default security checks provided by teler IDS.
//
// The glob pattern supports wildcards, allowing you to specify multiple files
// or a directory with matching files. For example, "/path/to/custom/rules/**/*.yaml"
// will load all YAML files in the "rules" directory and its subdirectories.
CustomsFromFile string `json:"customs_from_file" yaml:"customs_from_file"`
// Response is the configuration for custom error response pages when a request
// is blocked or rejected.
Response Response `json:"response" yaml:"response"`
// LogFile is the file path for the log file to store the security logs.
//
// If LogFile is specified, log messages will be written to the specified
// file in addition to stderr (if NoStderr is false).
LogFile string `json:"log_file" yaml:"log_file"`
// LogWriter is an io.Writer interface used for custom log message output.
//
// By default, log messages are written to the standard error (stderr) if
// NoStderr is set to false. However, you can customize the output destination
// for log messages by providing your own implementation of io.Writer to this
// field. When a custom LogWriter is assigned, log messages will be written to
// it in addition to LogFile and stderr (if NoStderr is false). This allows you
// to capture and handle log messages in a custom way, such as sending them to
// a remote logging service, storing them in a database, or handling them in a
// specialized manner.
LogWriter io.Writer `json:"-" yaml:"-"`
// NoStderr is a boolean flag indicating whether or not to suppress log messages
// from being printed to the standard error (stderr) stream.
//
// When set to true, log messages will not be printed to stderr. If set to false,
// log messages will be printed to stderr. By default, log messages are printed
// to stderr (false).
NoStderr bool `json:"no_stderr" yaml:"no_stderr"`
// NoUpdateCheck is a boolean flag indicating whether or not to disable automatic threat
// dataset updates.
//
// When set to true, automatic updates will be disabled. If set to false, automatic
// updates will be enabled. By default, automatic updates are enabled (false).
//
// If the InMemory is set to true, the NoUpdateCheck value will not have any effect
// or automatic updates will always be enabled.
NoUpdateCheck bool `json:"no_update_check" yaml:"no_update_check"`
// Development is a boolean flag that determines whether the request is cached or not.
//
// By default, development mode is disabled (false) or requests will cached.
Development bool `json:"development" yaml:"development"`
// InMemory is a boolean flag that specifies whether or not to load the threat dataset
// into memory on initialization.
//
// When set to true, the threat dataset will be loaded into memory, which can be useful
// when running your service or application on a distroless or runtime image, where file
// access may be limited or slow. If InMemory is set to false, the threat dataset will
// be downloaded and stored under the user-level cache directory on the first startup.
// Subsequent startups will use the cached dataset.
InMemory bool `json:"in_memory" yaml:"in_memory"`
// FalcoSidekickURL is the URL of the FalcoSidekick endpoint to which teler-waf's events
// will be forwarded.
//
// This field should be set to the URL of your FalcoSidekick instance, including the
// protocol & port (e.g. "http://localhost:2801").
FalcoSidekickURL string `json:"falcosidekick_url" yaml:"falcosidekick_url"`
// Verbose is a boolean flag that controls whether verbose logging is enabled.
// When set to true, it enables detailed and informative logging messages.
Verbose bool `json:"verbose" yaml:"verbose"`
}
 Source Files
¶
Source Files
¶
 Directories
¶
Directories
¶
| Path | Synopsis |
|---|---|
|
Package option provides functions for unmarshaling teler-waf configuration from JSON and YAML formats into the teler.Options struct.
|
Package option provides functions for unmarshaling teler-waf configuration from JSON and YAML formats into the teler.Options struct. |
|
Package request implements a set of utilities and structures for handling HTTP requests.
|
Package request implements a set of utilities and structures for handling HTTP requests. |
|
Package threat implements functionality for handling threat data and analyzing requests for threats.
|
Package threat implements functionality for handling threat data and analyzing requests for threats. |