Documentation
¶
Documentation
¶
Overview ¶
Package cmrdr provides methods to be able to discover and attack RTSP streams easily. RTSP streams are used by most IP Cameras, often for surveillance.
A simple example usage of the library can be found in https://github.com/Ullaakut/cameradar/tree/master/cameradar
The example usage is complete enough for most users to ignore the library, but for users with specific needs such as creating their own bruteforcing dictionary to access cameras, or running their own network scan, this library allows to use simple and performant methods to attack streams.
Index ¶
- Constants
- func GetCameraAdminPanelURL(stream Stream) string
- func GetCameraRTSPURL(stream Stream) string
- func NmapRun(targets, ports, resultFilePath string, nmapSpeed int, enableLogs bool) error
- func ParseTargetsFile(path string) (string, error)
- type Credentials
- type Curl
- type Curler
- type Options
- type Routes
- type Stream
- func AttackCredentials(c Curler, targets []Stream, credentials Credentials, timeout time.Duration, ...) ([]Stream, error)
- func AttackRoute(c Curler, targets []Stream, routes Routes, timeout time.Duration, log bool) ([]Stream, error)
- func Discover(targets, ports, nmapResultPath string, speed int, log bool) ([]Stream, error)
- func NmapParseResults(nmapResultFilePath string) ([]Stream, error)
- func ValidateStreams(c Curler, targets []Stream, timeout time.Duration, log bool) ([]Stream, error)
Constants ¶
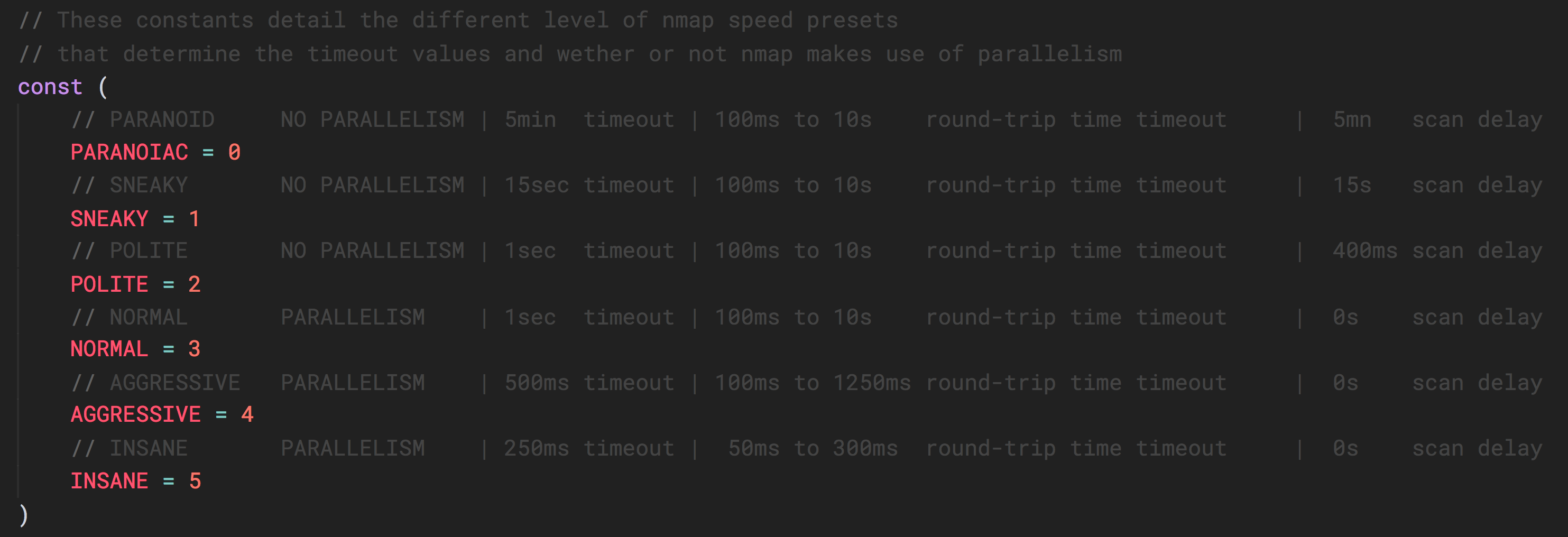
const ( // PARANOIAC NO PARALLELISM | 5min timeout | 100ms to 10s round-trip time timeout | 5mn scan delay PARANOIAC = 0 // SNEAKY NO PARALLELISM | 15sec timeout | 100ms to 10s round-trip time timeout | 15s scan delay SNEAKY = 1 // POLITE NO PARALLELISM | 1sec timeout | 100ms to 10s round-trip time timeout | 400ms scan delay POLITE = 2 // NORMAL PARALLELISM | 1sec timeout | 100ms to 10s round-trip time timeout | 0s scan delay NORMAL = 3 // AGGRESSIVE PARALLELISM | 500ms timeout | 100ms to 1250ms round-trip time timeout | 0s scan delay AGGRESSIVE = 4 // INSANE PARALLELISM | 250ms timeout | 50ms to 300ms round-trip time timeout | 0s scan delay INSANE = 5 )
These constants detail the different level of nmap speed presets that determine the timeout values and wether or not nmap makes use of parallelism
Variables ¶
This section is empty.
Functions ¶
func GetCameraAdminPanelURL ¶
GetCameraAdminPanelURL returns the URL to the camera's admin panel
func GetCameraRTSPURL ¶
GetCameraRTSPURL generates a stream's RTSP URL
func NmapRun ¶
NmapRun runs nmap on the specified targets's specified ports, using the given nmap speed.
func ParseTargetsFile ¶
ParseTargetsFile parses an input file containing hosts to targets
Types ¶
type Credentials ¶
type Credentials struct {
Usernames []string `json:"usernames"`
Passwords []string `json:"passwords"`
}
Credentials is a map of credentials usernames are keys and passwords are values creds['admin'] -> 'secure_password'
func LoadCredentials ¶
func LoadCredentials(path string) (Credentials, error)
LoadCredentials opens a dictionary file and returns its contents as a Credentials structure
func ParseCredentialsFromString ¶
func ParseCredentialsFromString(content string) (Credentials, error)
ParseCredentialsFromString parses a dictionary string and returns its contents as a Credentials structure
type Curl ¶
Curl is a libcurl wrapper used to make the Curler interface work even though golang currently does not support covariance (see https://github.com/golang/go/issues/7512)
type Curler ¶
type Curler interface {
Setopt(opt int, param interface{}) error
Perform() error
Getinfo(info curl.CurlInfo) (interface{}, error)
Duphandle() Curler
}
Curler is an interface that implements the CURL interface of the go-curl library Used for mocking
type Options ¶
type Options struct {
Target string `json:"target" validate:"required"`
Ports string `json:"ports"`
OutputFile string `json:"output_file"`
Routes Routes `json:"routes"`
Credentials Credentials `json:"credentials"`
Speed int `json:"speed"`
Timeout time.Duration `json:"timeout"`
}
Options contains all options needed to launch a complete cameradar scan
type Routes ¶
type Routes []string
Routes is a slice of Routes ['/live.sdp', '/media.amp', ...]
func LoadRoutes ¶
LoadRoutes opens a dictionary file and returns its contents as a Routes structure
func ParseRoutesFromString ¶
ParseRoutesFromString parses a dictionary string and returns its contents as a Routes structure
type Stream ¶
type Stream struct {
Device string `json:"device"`
Username string `json:"username"`
Password string `json:"password"`
Route string `json:"route"`
Address string `json:"address" validate:"required"`
Port uint `json:"port" validate:"required"`
CredentialsFound bool `json:"credentials_found"`
RouteFound bool `json:"route_found"`
Available bool `json:"available"`
}
Stream represents a camera's RTSP stream
func AttackCredentials ¶
func AttackCredentials(c Curler, targets []Stream, credentials Credentials, timeout time.Duration, log bool) ([]Stream, error)
AttackCredentials attempts to guess the provided targets' credentials using the given dictionary or the default dictionary if none was provided by the user.
func AttackRoute ¶
func AttackRoute(c Curler, targets []Stream, routes Routes, timeout time.Duration, log bool) ([]Stream, error)
AttackRoute attempts to guess the provided targets' streaming routes using the given dictionary or the default dictionary if none was provided by the user.
func Discover ¶
Discover scans the target networks and tries to find RTSP streams within them.
targets can be:
- a subnet (e.g.: 172.16.100.0/24)
- an IP (e.g.: 172.16.100.10)
- a hostname (e.g.: localhost)
- a range of IPs (e.g.: 172.16.100.10-20)
ports can be:
- one or multiple ports and port ranges separated by commas (e.g.: 554,8554-8560,18554-28554)
func NmapParseResults ¶
NmapParseResults returns a slice of streams from an NMap XML result file. To generate one yourself, use the -X option when running NMap.